Description : How does it work ? What is Bluejacking?
What is Bluejacking?
Bluejacking is a harmless prank played on people who have switched Bluetooth on their phones.It is not mobile hacking or hijacking its totaly different.
Bluejacking is a kind of practical joke played out between Bluetooth-enabled devices, bluejacking takes advantage of a loophole in the technology's messaging options that allows a user to send unsolicited messages to other nearby Bluetooth owners.
Blue is taken from Bluetooth, the technology bluejacking uses.
Jacking is derived from both "ajack" and "hijacking"
Even thought bluejacking does not resemble hijacking.There is no accessing or taking private data from your victim's device.
Bluejacking can be used to send messages to other Bluetooth devices that are within range of 10 meters on mobile phones, but laptops and other instrument with high power transmitters can reach up to 100 meters. With recent developments, it can also be used to send sounds and images. A person receiving these messages might think that his phone is malfunctioning. In reality, it is just bluejacked.
Few prople say the term “Bluejacking” originated with a user named ajack on esato.com. Some people say that the term bluejacking comes from Bluetooth and hijacking. While that certainly sounds logical, a bluejacker doesn't hijack anything, he just send a contact to the recipient's device. Both parties have absolute control over their devices, and a bluejacker will not be able to take control of your phone or steal your personal information.
Bluejacking can be used for chatting and blind dating, a popular practice in Europe, where Bluejacking first started. It can be dangerous to share personal information with a person whose identity is not known to you.
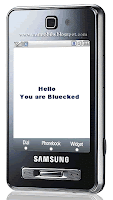 Bluejacking is very easy to do. A person just creates a new fake contact in his phone book and inserts the actual message to be sent in the contact’s name field. The “bluejacker” then chooses any of the nearby mobile phone devices having Bluetooth enabled and sends the message using the “send contact information” function. The message appears on the screen of the victim, who has no way of finding out where the message came from.Although some of the newer Nokia's have the ability to reject an incoming bluejack. Butmost attempts will be sent right through, and then on the victim's phone, they will see the message (name), and it will ask if they want to accept or reject it. If they accept it, it's added to their phone, if they reject, the card is not added, but they have seen the message.
Bluejacking is very easy to do. A person just creates a new fake contact in his phone book and inserts the actual message to be sent in the contact’s name field. The “bluejacker” then chooses any of the nearby mobile phone devices having Bluetooth enabled and sends the message using the “send contact information” function. The message appears on the screen of the victim, who has no way of finding out where the message came from.Although some of the newer Nokia's have the ability to reject an incoming bluejack. Butmost attempts will be sent right through, and then on the victim's phone, they will see the message (name), and it will ask if they want to accept or reject it. If they accept it, it's added to their phone, if they reject, the card is not added, but they have seen the message.
Legal Issues:
Bluetooth can be used as a weapon to compromise privacy. Whenever the Bluetooth service is not required, just turn it off to protect against unnecessary trouble. Modern phones automatically shut down Bluetooth service after 5 to 10 minutes to avoid problems.


Comments :
Post a Comment